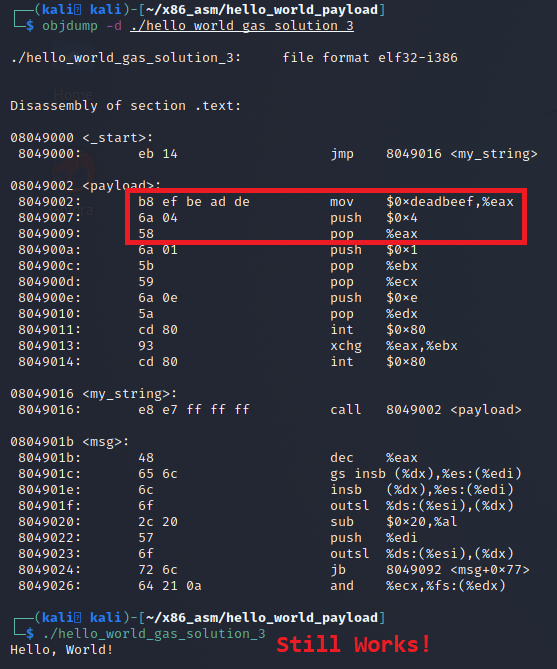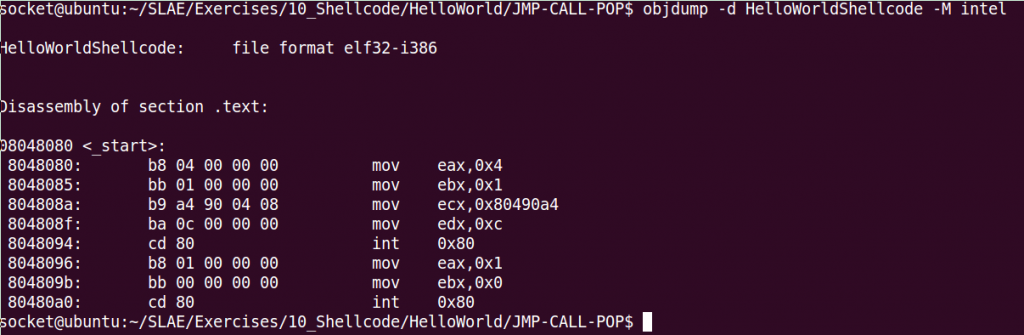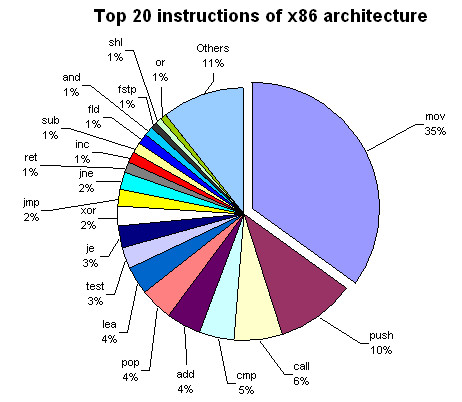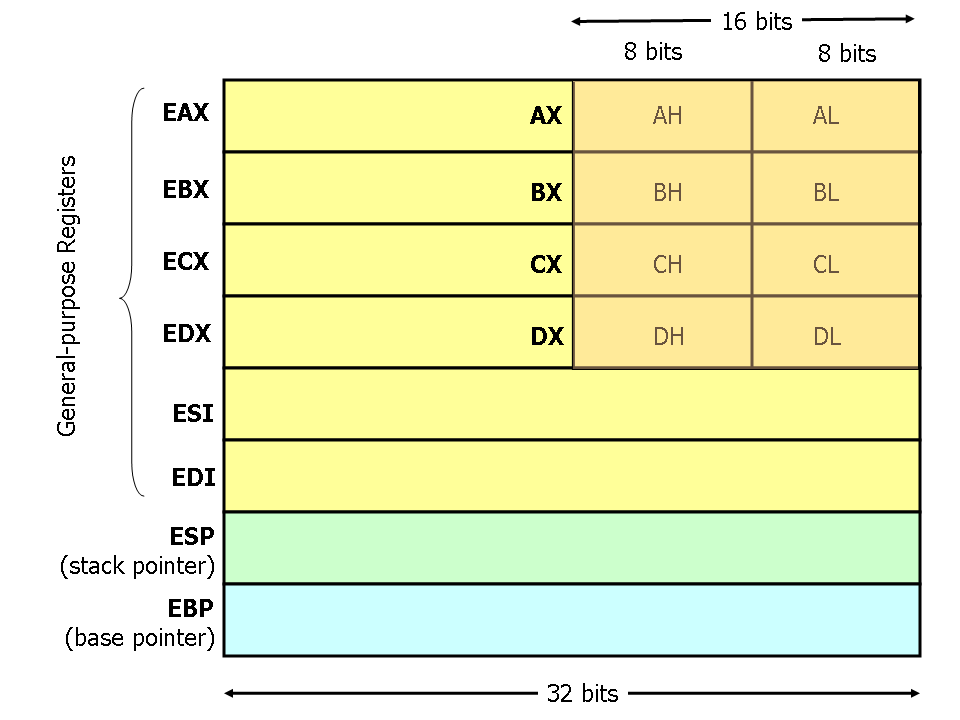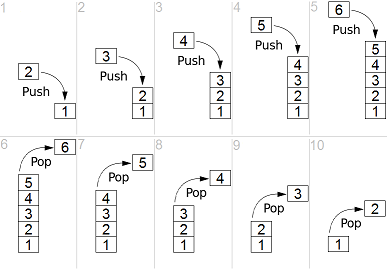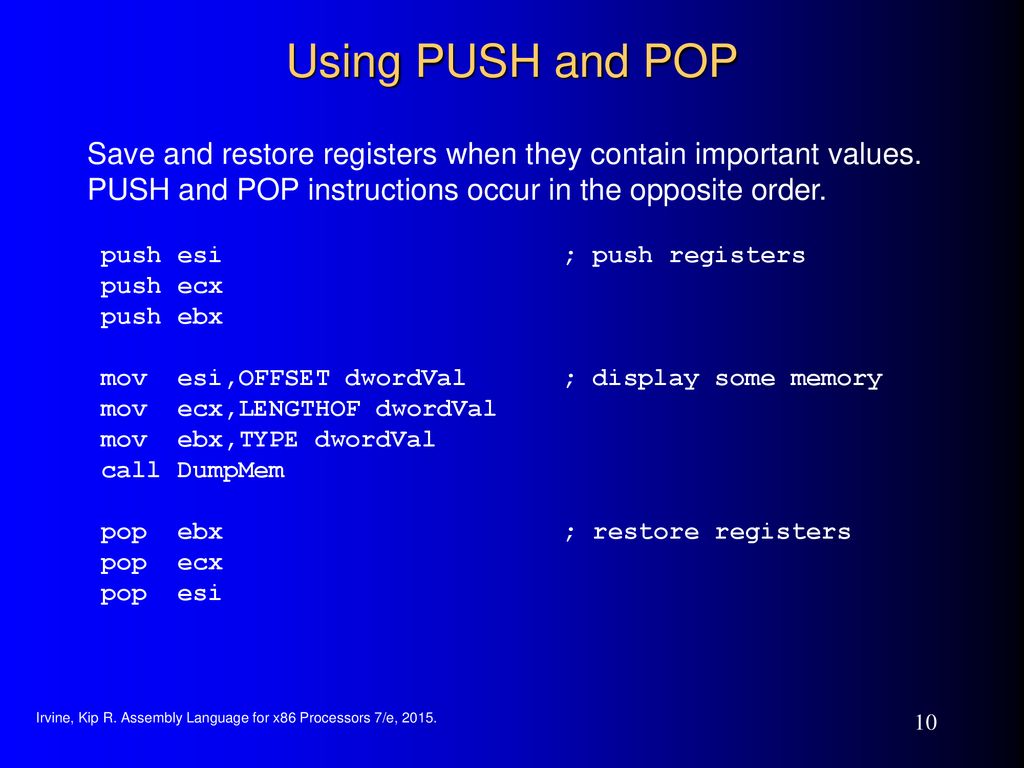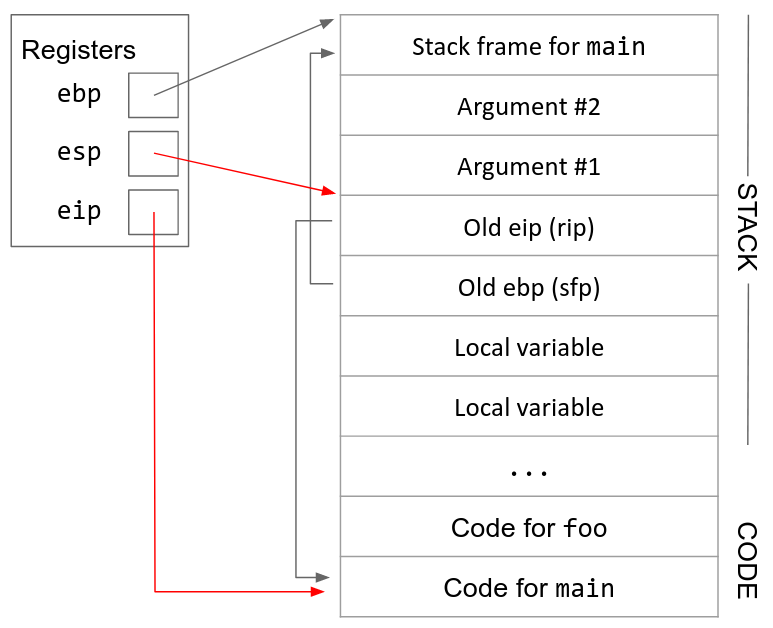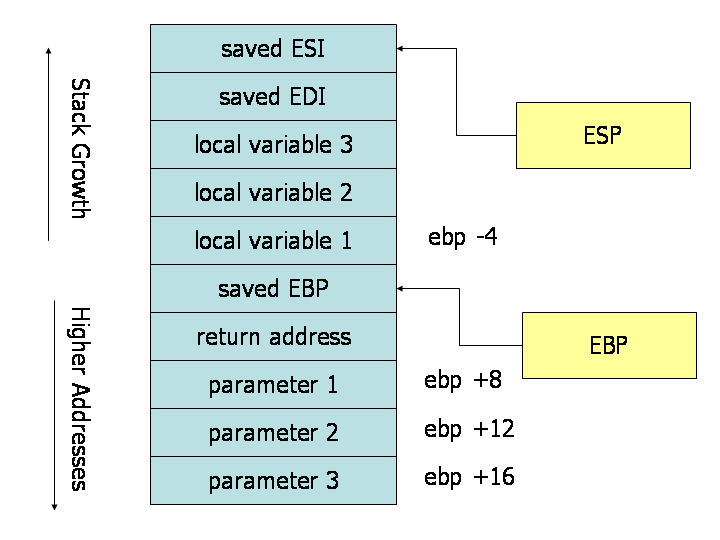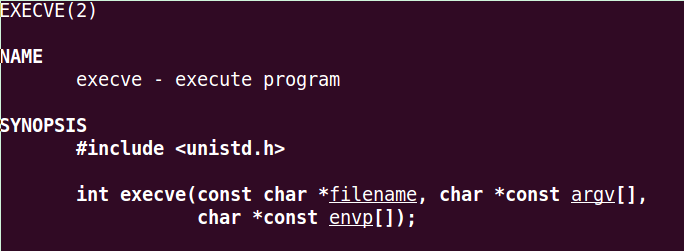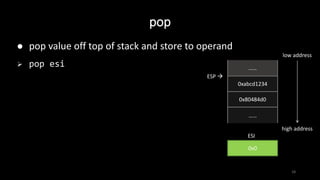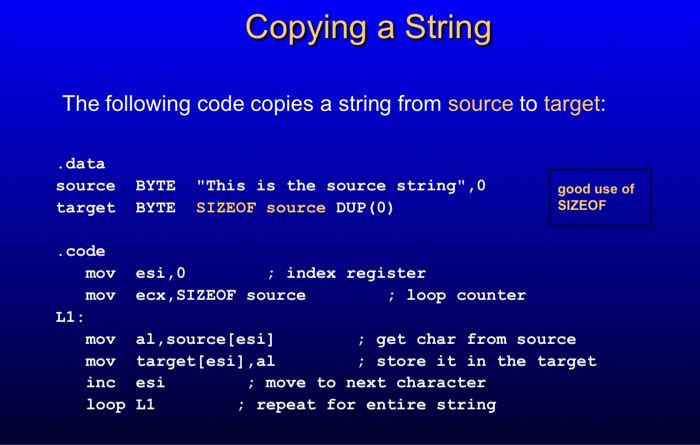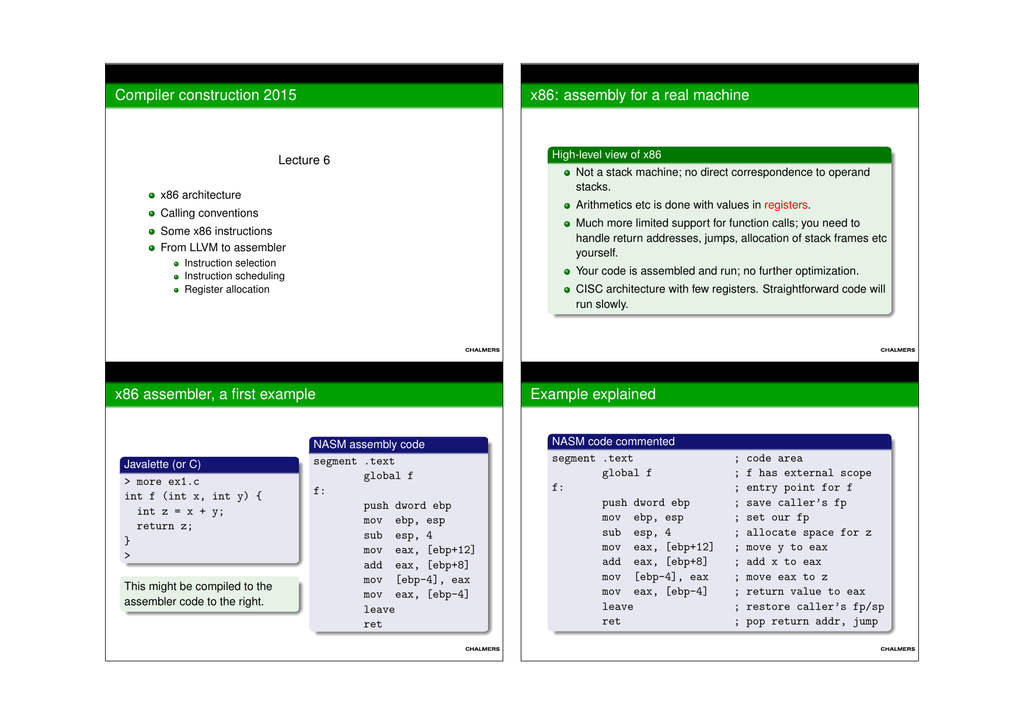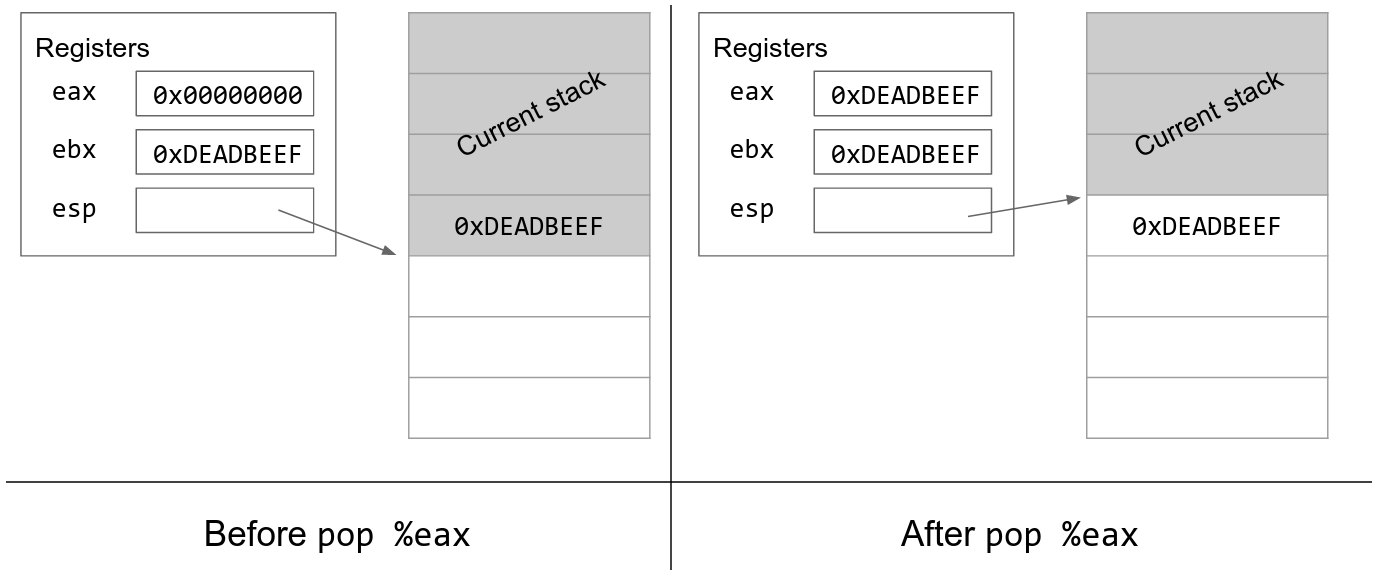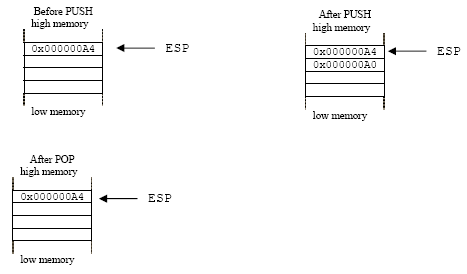
The details of C function stack (and heap) operation when function call is made (caller) and returned (callee) on personal computers

x86 - What happens exactly under the hood to Assembly `push`, `pop`, `call`, and `ret` operations? - Stack Overflow
Incorrect PCode for x86 pop Instructions with Stack Pointer Operands · Issue #4282 · NationalSecurityAgency/ghidra · GitHub

winapi - What is the purpose of the pause x86 instruction and the loop in the GetSystemTimeAsFileTime function disassembly? - Stack Overflow
Outline The stack Push and pop instructions Offset-based stack accesses Argument and return registers Sharing registers Preservi