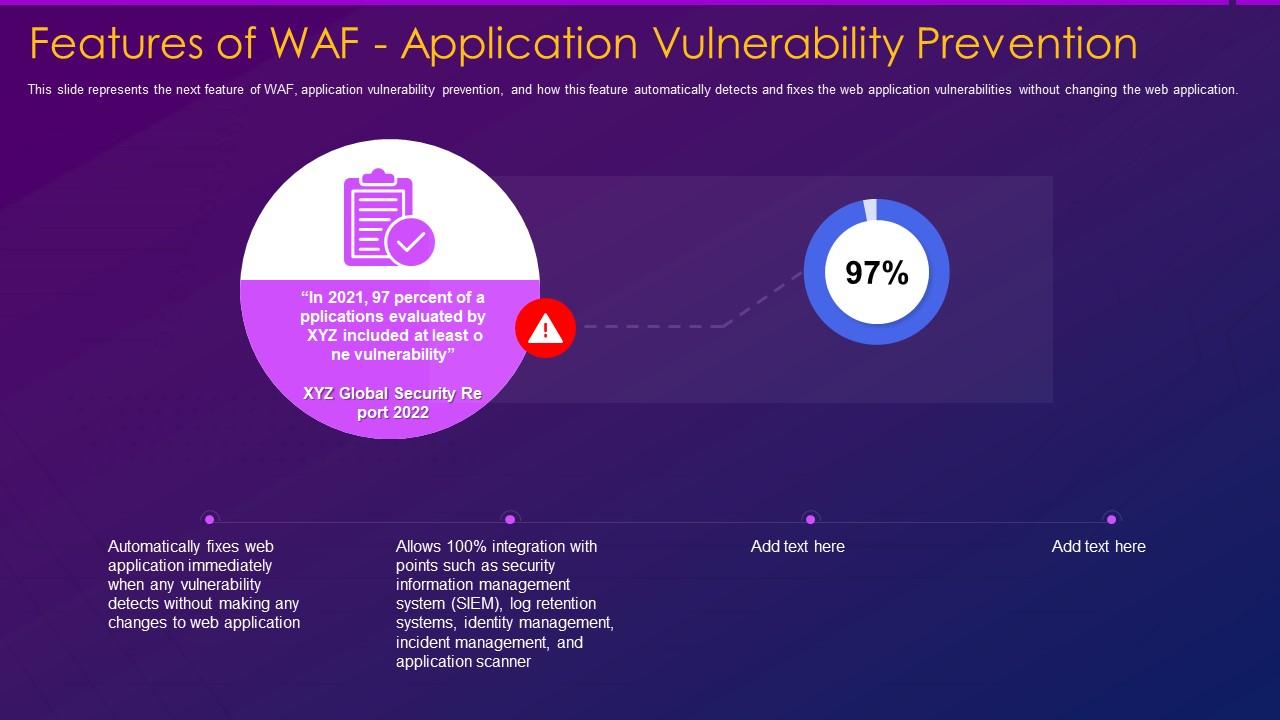
Features Of Waf Application Vulnerability Prevention Web Application Firewall Waf It | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

How to Protect Your Website with Web Vulnerability Scanner (WVS) and Web Application Firewall (WAF) - tech.netonboard.com