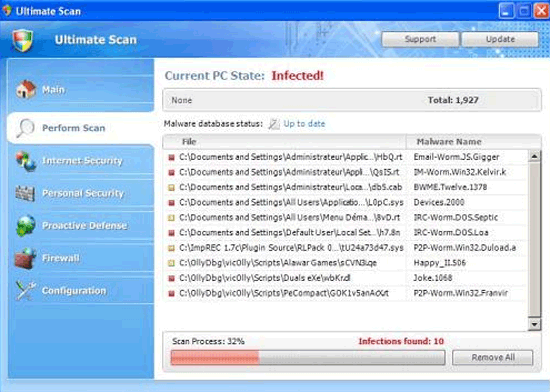
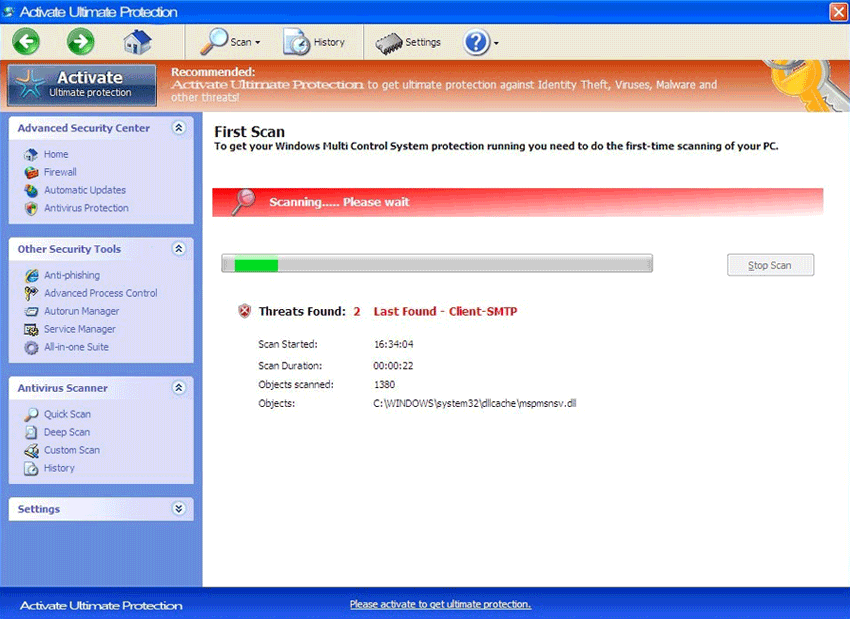
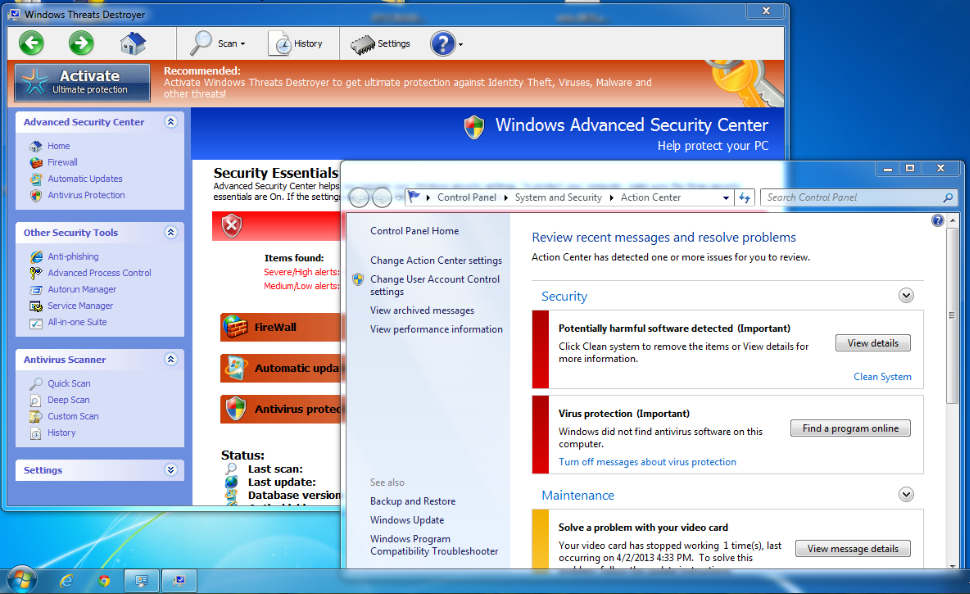
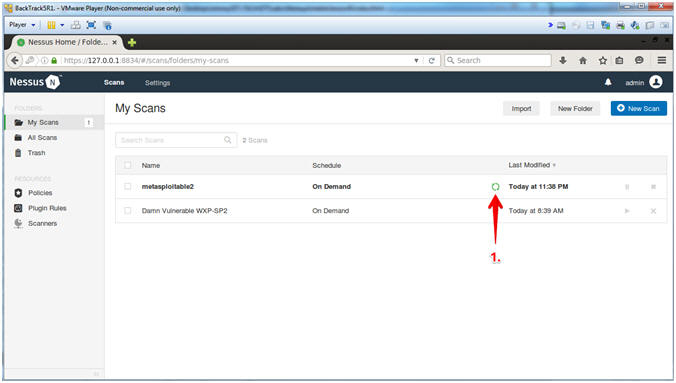
Router Exploit Kits: An overview of RouterCSRF attacks and DNS hijacking in Brazil - Avast Threat Labs

Zero-Day Exploit: Countdown to Darkness (Cyber-Fiction): Rob Shein, David Litchfield, Marcus Sachs: 9781931836098: Books - Amazon

AnchorWatch - A Rogue Device Detection Script for Windows with Email Alerts. I wrote a PowerShell script that scans subnet(s) every X minutes and sends email alerts on each discovery. : r/netsec