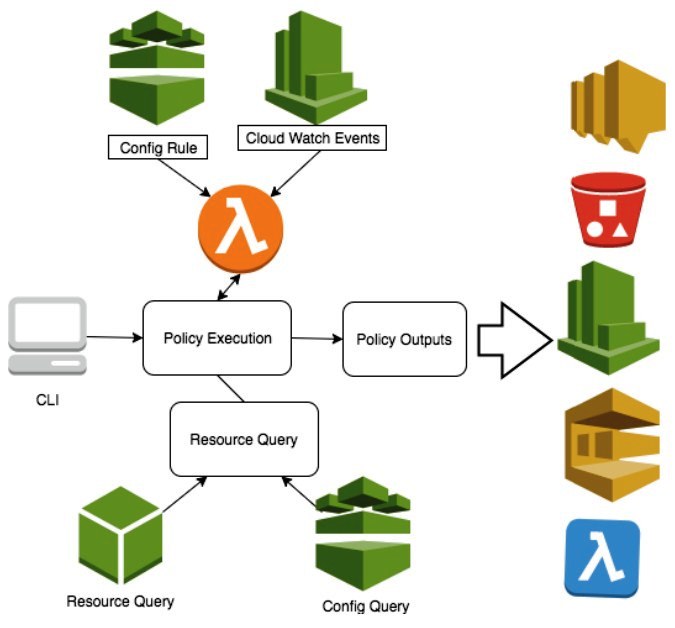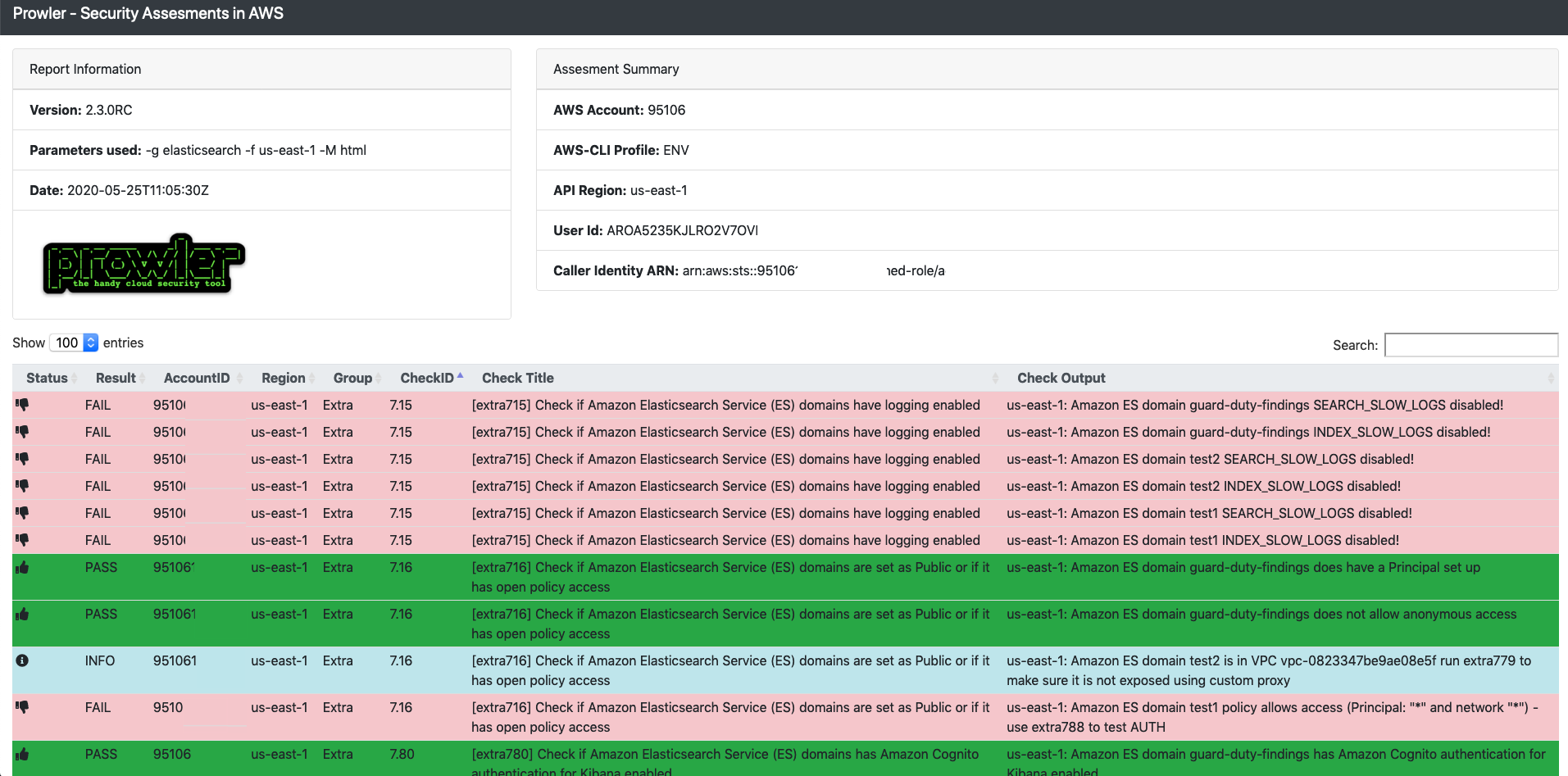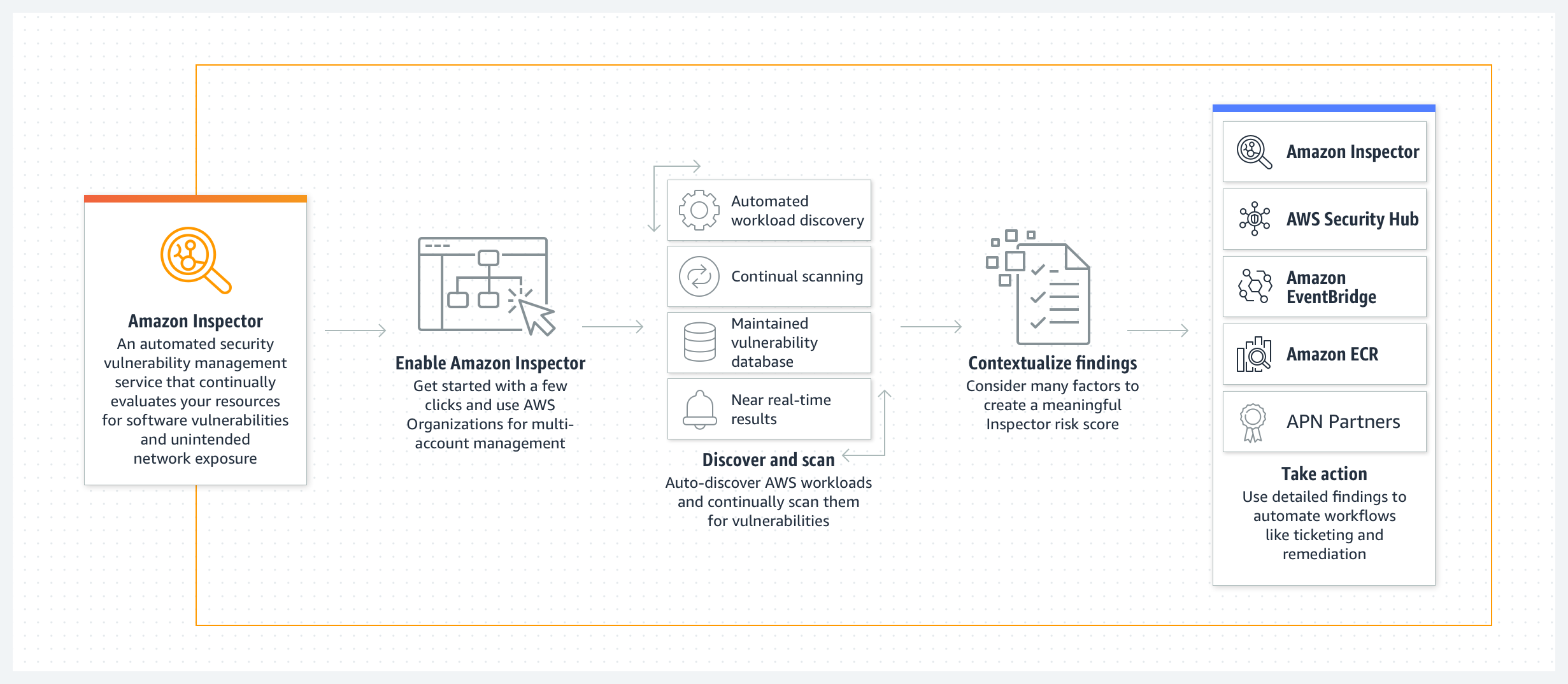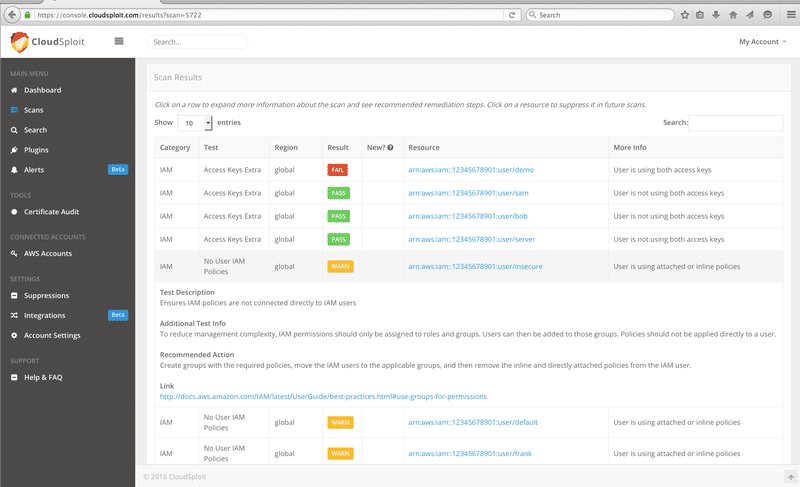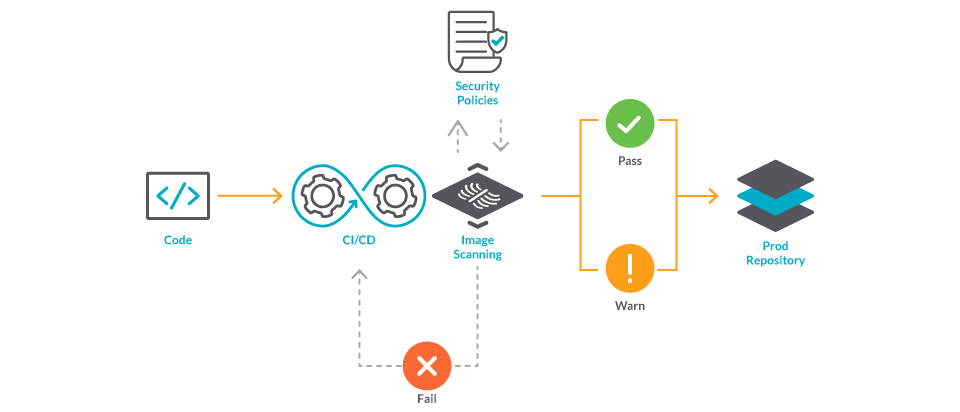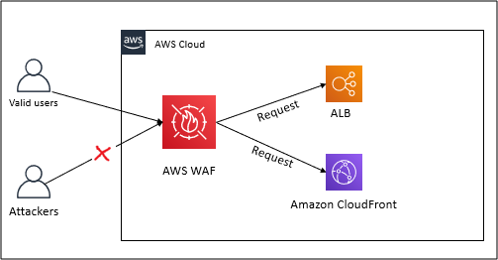
Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium

Identifying and resolving security code vulnerabilities using Snyk in AWS CI/CD Pipeline | AWS DevOps Blog

Top Security Scanning and Vulnerability Management Tools |AWS| | by Kubernetes Advocate | AVM Consulting Blog | Medium